Denial of Service in TYPO3 Bookmark Toolbar
TYPO3 through 12.4.6 allows, due to insufficient input validation, manipulated data saved in the bookmark toolbar of the backend user interface causes a general error state, blocking further access to the interface. Exploiting this vulnerability requires an administrator-level backend user account.
Description
The Typo3 backend allows saving bookmarks via the toolbar.
The request to create a bookmark is not verified.
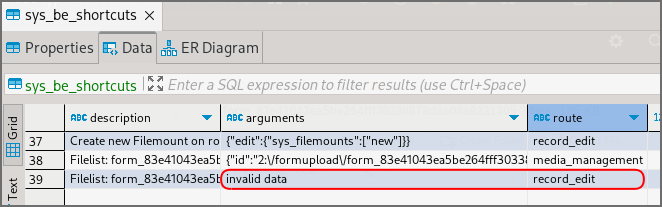
Typically, a JSON object containing the necessary data is sent to the server for the arguments parameter. The routeIdentifier parameter must contain one of several possible values (e.g., record_edit or media_management).
To carry out the DoS attack, the value of the arguments parameter (a valid example is shown in the following code block) must be set to an invalid value. An invalid value is any input that is not in JSON format or does not contain an edit attribute when routeIdentifier=record_edit.
{"id":"2:\/formupload\/form_83e41043ea5be264fff30338878dae08a8231305\/"}
After modifying a database entry with the value routeIdentifier=record_edit, the Typo3 backend becomes unusable. Since admin users have the ability to define these bookmarks globally for all users, this results in the backend being inaccessible to everyone.
The incorrect database entry must be manually corrected to restore the application's functionality.
Assigned CVE
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-34537
Affected Component
https://github.com/TYPO3/typo3 (typo3/cms-backend)
Attack Type
Remote
Impact Code Execution
False
Attack vectors
To exploit the vulnerability an attacker requires a valid user account in the Typo3 backend instance with the rights to create a bookmark of type record_edit. After the attack no users will be able to access the Typo3 Backend until the malicious entry is fixed directly in the database.
Reference
https://github.com/TYPO3/typo3/security/advisories/GHSA-ffcv-v6pw-qhrp
Discoverer
Mirko Richter (mgm security partners), Hendrik Eichner (mgm security partners)